Abstract - In the digital age, the escalating sophistication of cyber threats necessitates innovative solutions to mitigate financial losses. Cybersecurity insurance emerges as a crucial tool, offering protection against various cyber incidents such as data breaches, system hacking, and ransomware attacks. This paper investigates the concept of cybersecurity insurance, its coverage nuances, and the leading providers dominating the market.
1. Introduction
In an era where digital technologies pervade every aspect of business operations, cybersecurity has become a paramount concern for organisations worldwide. The increasing frequency and sophistication of cyber threats pose significant challenges, leading to financial losses, reputational damage, and operational disruptions. In response to these evolving risks, cybersecurity insurance has emerged as a proactive measure to mitigate the financial impact of cyberattacks. This paper delves into the realm of cybersecurity insurance, examining its definition, relevance, and potential benefits in safeguarding businesses against cyber risks.
The Grant Thornton International Business Report's (IBR) is the world's leading mid-market business survey, interviewing approximately 5,000 senior executives biannually in listed and privately held companies all over the world. The results from the first quarter of 2024 underscore the growing importance of cybersecurity. With 61% of South African businesses prioritising cybersecurity and data privacy measures, and 61% expressing interest in advanced technologies such as Artificial Intelligence (AI), the data shows that cybersecurity is widely recognised as critical in mitigating financial losses, reputational harm, and operational disruptions caused by cyber threats. This emphasis on cybersecurity coincides with the growing use of cybersecurity insurance as a proactive strategy against developing risks, highlighting its importance in protecting enterprises from cyber hazards in today's digital landscape. This paper delves into the realm of cybersecurity insurance, examining its definition, relevance, and potential benefits in safeguarding businesses against cyber risks.
2. What is Cyber Insurance?
Cyber insurance, also known as cyber risk insurance or cyber liability insurance, is a specialised form of insurance designed to protect businesses and individuals from internet-based risks and liabilities. Unlike traditional insurance policies that primarily cover physical assets, cybersecurity insurance focuses on mitigating financial losses arising from cyber incidents such as data breaches, malware attacks, and ransomware extortion. It provides coverage for various expenses related to cyber incidents, including forensic investigations, data restoration, legal fees, regulatory fines, and crisis management.
3. Current Cyber Threats and Relevant Costs of Each Attack
The contemporary cyber threat landscape is characterised by a diverse array of malicious activities orchestrated by cybercriminals with varying motives. Understanding these threats is crucial for assessing the potential impact on businesses and the necessity of cybersecurity insurance coverage.
3.1 Cyber Threat Landscape
3.1.1 Malware Attacks
Malware, a prevalent form of cyber threat, inflicts substantial financial losses on organisation. According to the "2021 Cost of Cybercrime Study" by Accenture, the average cost of a malware attack amounts to $2.6 million, encompassing expenses related to detection, containment, recovery, and investigations.
3.1.2 Ransomware Incidents
Ransomware, characterised by threats to publish or block access to data unless a ransom is paid, has witnessed a surge in incidents. The "2022 Cybersecurity Report" by Cybersecurity Ventures reveals that the cost of ransomware attacks is projected to reach $20 billion, with organisations facing an average ransom demand of $112,000.
3.1.3 Phishing Schemes
Phishing schemes, wherein cybercriminals impersonate legitimate entities to obtain sensitive information, have emerged as a significant financial threat. According to the "2021 Data Breach Investigations Report" by Verizon, the financial impact of phishing attacks has quadrupled over the past six years, with U.S. companies incurring an average annual cost of $14.8 million in 2021.
3.1.4 DDOS/IoT Attacks
DDoS attacks, aimed at rendering online services unavailable by overwhelming them with traffic, impose substantial financial burdens on businesses. The "The Cost of DDoS Attacks" report by Kaspersky highlights that small to medium enterprises face an average cost of $120,000, while large enterprises could incur over $2 million in damages.
3.2 Financial Implications
3.2.1 Global Average Cost of Data Breach (2023)
The global average cost of a data breach surged to $4.45 million in 2023, marking a 15% increase over the previous three years. According to the "2023 Cost of a Data Breach Report" by IBM Security, apart from immediate financial ramifications, data breaches also erode long-term reputation and customer trust.
3.2.2 Global Annual Cost of Cybercrime (Projected for 2024)
The projected global annual cost of cybercrime is estimated at $9.5 trillion USD in 2024, highlighting the staggering financial impact of cyber threats. As per the "Cybersecurity Ventures Cybercrime Report 2024" by Cybersecurity Ventures, cybercrime, if treated as a country, would rank as the world's third-largest economy.
3.2.3 Remediation Time for Cyber Attacks
The time taken to remediate cyber-attacks varies depending on factors such as attack complexity and organisational preparedness. However, prolonged response times escalate costs, encompassing lost business, regulatory fines, and recovery efforts. According to "The Cost of Cybercrime Study 2021" by Accenture, while specific statistics on average remediation times are not readily available, it's clear that rapid and effective response to cyber-attacks is crucial in minimizing their financial impact.
4. How Cybersecurity Insurance Can Alleviate These Costs
Cybersecurity insurance is a modern solution designed to mitigate financial losses from cyber threats. It covers costs related to data breaches, system hacking, ransomware attacks, and more. By covering ransom payments, malware remediation, and other costs, cyber policies can help companies limit their damage, recover more quickly, and raise their overall level of cyber resilience. The average annual cost of a phishing scam in 2021 is $14.8 million for a 9,600-employee organisation, or slightly more than $1,500 per employee. Therefore, having cybersecurity insurance can significantly reduce the financial burden of these attacks.
5. What Can You Be Insured For?
Cyber insurance coverage is not one-size-fits-all; it varies based on specific business needs, industry, and data types. This section explores the intricacies of cyber insurance coverage, distinguishing between first-party and third-party coverage. It sheds light on how these options cater to different aspects of cyber incidents, including data recovery costs and damage suffered by external parties.
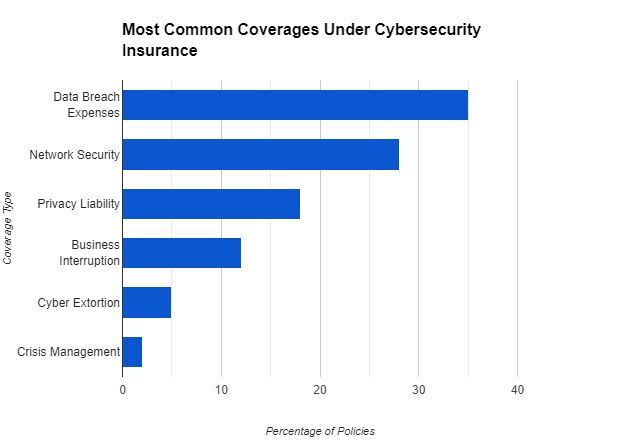
The figure above illustrates the most common coverage types in cyber insurance policies along with the corresponding percentages of policies offering each type of coverage. The Figure above is based on information from various sources, including IBM Security, Beazley, and Security.org
5.1 Data Breach Expenses
Data breaches expose sensitive personally identifiable information (PII), putting individuals at risk and incurring substantial expenses for organisations. IBM Security's "2023 Cost of a Data Breach Report" indicates that cyber insurance coverage for data breach expenses reimburses costs such as credit monitoring for affected individuals, legal fees for investigations and compliance, and data recovery costs. With most data breaches involving sensitive PII, this coverage serves as a cornerstone of cybersecurity insurance policies.
5.2 Network Security
Robust network security is essential in preventing data breaches and safeguarding organisations against cyber threats. Cyber insurance coverage for network security protects against lawsuits arising from network security failures or breaches that cause third-party harm, such as customer data loss or privacy violations. According to Cybersecurity Ventures' "2022 Cybersecurity Report," network vulnerabilities were exploited in a significant portion of data breaches, emphasising the importance of this coverage.
5.3 Private Liability
Expanding Your Safety Net: Beyond network security, your online activities can pose risks. This coverage shields you from personal liability claims due to data breaches or privacy violations arising from, say, social media missteps or employee negligence. In 2022, data privacy lawsuits increased by 32%, underlining the need for this protection. Its average cost of US$75,000 per claim offers peace of mind for unforeseen situations.
5.4 Business Interruption
Cyber-attacks can disrupt operations, leading to lost revenue, productivity, and customer trust. Accenture's "The Cost of Cybercrime Study 2021" indicates that business interruption coverage reimburses lost income and additional expenses incurred due to attack-induced disruptions, ensuring organisations can weather the storm and bounce back quickly. With cyberattacks causing prolonged downtime, this coverage bridges the financial gap and facilitates business continuity.
5.5 Cyber Extortion
Ransomware attacks pose significant threats to organisations, with attackers demanding ransom payments to restore access to encrypted data. CrowdStrike's "Ransomware Threat Report 2022" states that cyber extortion coverage offers a lifeline by reimbursing ransom payments within stipulated limits and subject to specific policy conditions. Despite the ethical and legal implications, this coverage provides organsations with a means to mitigate the financial impact of ransomware attacks.
5.6 Crisis Management
The aftermath of a cyberattack can tarnish an organisation's reputation and erode customer trust. Cybersecurity Ventures' "2022 Cybersecurity Report" highlights that crisis management coverage provides support for managing the reputational damage caused by a breach, covering services like crisis communication experts, media relations specialists, and customer outreach programs. By helping organisations navigate the public eye and rebuild trust effectively, this coverage mitigates the long-term impact of cyber incidents.
In conclusion, the increasing frequency and complexity of cyber threats emphasise the necessity for strong cybersecurity measures. The Grant Thornton International Business Report underlines the global business community's recognition of cybersecurity's importance, alongside projections of significant global costs attributed to cybercrime. Cybersecurity insurance emerges as a proactive approach to risk management, providing financial protection and aiding in swift recovery from cyber incidents. By covering expenses like data breaches, ransomware attacks, and system hacking, cyber insurance lightens the financial burdens on businesses. Additionally, the diverse coverage options, from data breach costs to crisis management assistance, cater to various organisational needs. Ultimately, cybersecurity insurance is integral to comprehensive cybersecurity strategies, empowering businesses to navigate today's evolving threat landscape with resilience and confidence.
7. How SNG Grant Thornton can assist: A methodical approach.: A Methodical Approach
Considering the massive impact of cyber-attacks on business, organisations must be pro-active across all spheres to prepare for it. We stand by our clients, helping them brace for potential cybersecurity threats, ensuring continuous protection, effectively responding to incidents, and driving improvements to enhance their cybersecurity capabilities. This approach is particularly crucial in meeting the demands of cybersecurity insurance. Our steadfast methodology, detailed in the steps below, is designed to help you identify, protect, detect, respond, and recover from cyber-attacks:
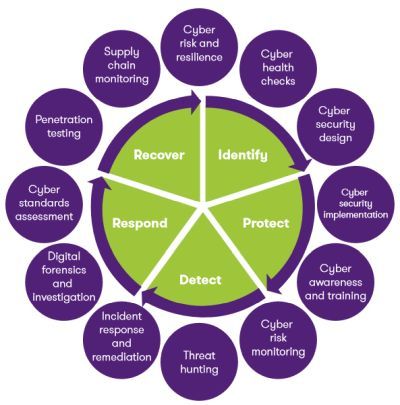
7.1 Identify: Identify cyber security risks and vulnerabilities
We help organisations understand their current exposure to cybersecurity risk and support them develop an effective security capability. Our services include cybersecurity risk and threat assessments; cyber health checks; security policy development; security process or technical assessments; and third-party and supply chain cybersecurity assurance.
7.2 Protect: Protect critical infrastructure assets
We develop and implement the technical framework and broader processes required to protect your organisation. Our services include security architecture; security technology implementations; security process design and implementation; identity and access management; privacy and data protection; GDPR and POPI advisory; data classification; enterprise application integrity; security awareness training; cyber security audits; security hardening; cloud security; vulnerability assessments; and penetration testing.
7.3 Detect: Detect the occurrence of a cyber event
We help organisations develop and implement the appropriate activities to detect the occurrence of a cyber security event. Our services include Security log review and monitoring (SOC, SIEM), Threat Hunting and Cyber Risk Monitoring.
7.4 Respond: Respond to a detected event
We work with organisations to support and monitor their cybersecurity operations and help them respond rapidly and forensically in the event of a security or data breach. Our services include digital forensics and investigations, incident response and monitoring. Our services include digital forensics and investigations, incident response and monitoring.
7.5 Recover: Recover from a cyber event
We help organisations develop and implement the appropriate activities, prioritised through the organisation's risk management process, to restore the capabilities or critical infrastructure services that were impaired through a cyber security event. Our services include advisory and assurance on business continuity management, disaster recovery and cyber insurance.
8. Enhancing Cybersecurity Compliance with Our Services
Navigating the intricate world of cybersecurity can be challenging, especially when it comes to meeting the requirements of cyber insurance. Let's explore how our tailored services can empower your organisation to not only meet these requirements but also enhance your overall cybersecurity posture:
8.1 Risk Assessment Services
Our risk assessment services are designed to identify and evaluate the cyber risks your organisation faces. This is a crucial step in understanding your organisation's threat landscape and vulnerabilities. By managing these risks effectively, we can help you meet the risk management requirements of your cyber insurance policy. Furthermore, a thorough risk assessment can potentially lower your insurance premiums as it demonstrates to insurers that you are actively managing your cyber risks.
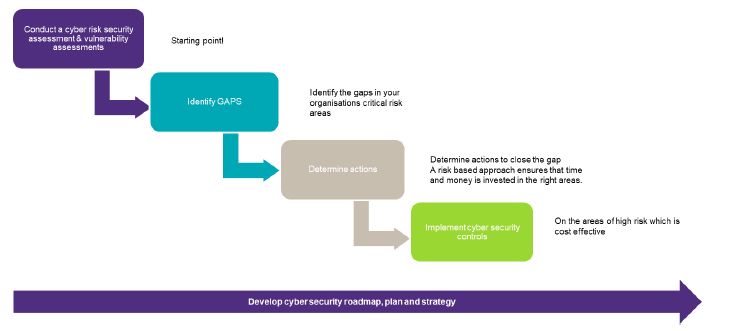
8.2 Building Cyber Resilience
We work to enhance your organisation's cyber resilience, which is its ability to prevent, withstand, and recover from cybersecurity incidents. This is not only vital for maintaining business continuity but also a key factor that cyber insurance providers consider. A cyber-resilient organsation is likely to suffer less damage from a cyber incident, which can lead to fewer and smaller insurance claims. Thus, building cyber resilience can help you maintain compliance with your cyber insurance policy and potentially reduce your premiums.
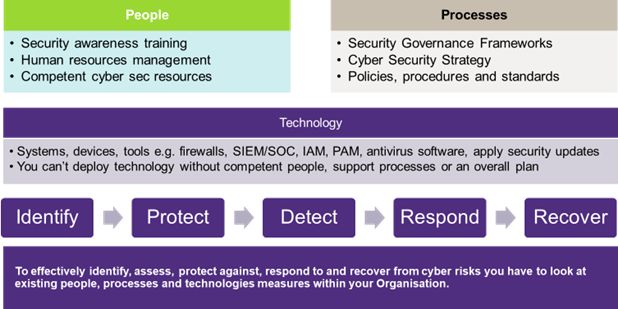
8.3 Cyber Maturity Development
We assist in developing your organisation's cyber maturity, which is its ability to manage security risks over time. A high level of cyber maturity indicates that your organisation has robust security controls and processes in place and is prepared for potential incidents. This can reassure your cyber insurance provider that you are a low-risk client, helping you secure more favourable insurance terms and potentially lower premiums.
9. Conclusion
Given the evolving cyber threat landscape and its profound financial implications, cybersecurity insurance emerges as a strategic imperative for organisations. By transferring some of the financial risks associated with cyber-attacks to insurers, businesses can bolster their resilience against unforeseen contingencies. However, the efficacy of cybersecurity insurance hinges on several factors, including policy coverage, premium costs, and insurer reputation. Moreover, the nascent nature of cyber risk assessment poses challenges in accurately quantifying and pricing cyber insurance policies.
Remember, prevention is always better than cure, so implementing robust security measures alongside insurance remains crucial. With the right combination of awareness, protection, and financial preparedness, you can navigate the digital landscape with greater confidence, even amidst the evolving cyber threat landscape.
References
- IBM: What is Cyber Insurance
- Cisco: What Is Cyber Insurance
- Accenture. "2021 Cost of Cybercrime Study."
- Cybersecurity Ventures. "2022 Cybersecurity Report."
- Verizon. "2021 Data Breach Investigations Report."
- Kaspersky. "The Cost of DDoS Attacks."
- IBM Security. "2023 Cost of a Data Breach Report."
- Cybersecurity Ventures. "Cybersecurity Ventures Cybercrime Report 2024."
- Accenture. "The Cost of Cybercrime Study 2021."
- IBM Security. "2023 Cost of a Data Breach Report."
- CrowdStrike. "Ransomware Threat Report 2022."
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.
We operate a free-to-view policy, asking only that you register in order to read all of our content. Please login or register to view the rest of this article.


