- within Technology topic(s)
- in European Union
- within Technology, Law Department Performance and Strategy topic(s)
- in European Union
- with readers working within the Utilities industries
Abstract - In the rapidly evolving realm of technology, cybersecurity stands as a paramount concern for organisations globally. As we delve close to the halfway mark of 2024, the landscape presents several challenges that demand proactive measures and strategic planning. This research paper delves into the most pressing cybersecurity challenges faced by organisations and offers recommendations for mitigation. The challenges analysed include the cyber workforce shortage, generative AI attacks, the cost of cyberattacks, and the necessity for cybersecurity transformation. Recommendations encompass promoting cyber education, enhancing awareness about social engineering tactics, crisis simulations for incident response preparedness, fostering collaboration, and empowering employees as the frontline defence. Embracing these strategies is imperative for organisations to fortify their cybersecurity defences and mitigate the evolving threats.
Introduction
Cybersecurity threats continue to escalate, posing significant risks to businesses, governments, and individuals alike. In this paper, we delve into the challenges that organisations confront in 2024 and propose strategies to enhance their security posture. The ever-changing nature of cyber threats necessitates continuous adaptation and proactive measures to safeguard sensitive data and critical infrastructure.
The Evolving Threat Landscape: Why Cybersecurity Matters More Than Ever
The Cybersecurity team at SNG Grant Thornton understands the ever-present threat landscape organisations face in today's digital world. Malicious actors, ranging from sophisticated nation-states to financially motivated cybercriminals, constantly evolve their tactics, relentlessly seeking to exploit vulnerabilities in your systems and applications. The consequences of a successful cyberattack can be devastating, leading to:
- Data breaches: Sensitive information like customer data, financial records, and intellectual property can be exposed, leading to significant financial losses and reputational damage.
- Financial losses: Businesses can incur significant costs due to downtime, data recovery, regulatory fines, and legal fees associated with cyberattacks.
- Reputational damage: A cyberattack can erode public trust and damage your brand reputation, making it difficult to attract and retain customers and partners.
- Operational disruption: Cyberattacks can disrupt critical business operations, leading to lost productivity, revenue, and customer satisfaction.
Traditional external audit/assurance processes often focus on financial health and internal controls but may not delve deeply into the specific vulnerabilities and risks posed by the digital environment. This leaves organisations exposed to significant cyber threats.
Key Challenges
1. Cyber Workforce Shortage
The scarcity of skilled cybersecurity professionals remains a pressing challenge, with over four million unfilled cybersecurity jobs globally. According to the "(ISC)2 Cybersecurity Workforce Study, 2021," the shortage persists, highlighting the need for urgent action1. To address this, organisations must focus on cyber education, promoting cybersecurity awareness and education at all levels to nurture a cybersecurity-aware culture1. Additionally, investing in upskilling programmes is essential to bridge the workforce gap and equip employees with necessary skills. Fostering foundational cyber skills among employees is also crucial, empowering them to identify and mitigate potential threats.
2. Generative AI Attacks
Social engineering attacks, facilitated by generative AI tools, pose a substantial threat due to their personalised nature. According to research by Biggio et al. (2019), these attacks leverage adversarial pattern recognition, making them increasingly difficult to detect2. To combat this challenge, organisations should focus on enhancing awareness by educating employees about social engineering tactics and raising awareness about the risks associated with them. Additionally, developing robust mechanisms to detect and mitigate deepfake content, including the deployment of AI-driven detection tools, is essential. Encouraging vigilance across all departments and fostering a culture of scepticism towards unsolicited communications and requests is also critical.
3. Cost of Cyberattacks
The financial impact of cyberattacks is staggering, with the global cost projected to exceed USD 10.5 trillion by the end of 2024. According to the "Cybersecurity Almanac 2021: 5-Year Outlook & Cybercrime Costs & Predictions," this represents a significant increase in cybercrime costs2. To mitigate this challenge, organisations should consider incident response preparedness by conducting regular crisis simulations to test response plans and ensure readiness to mitigate the impact of cyber incidents. Collaborating across functions to identify vulnerabilities and develop effective mitigation strategies is crucial. Investing in continuous development initiatives to empower cybersecurity professionals and enhance their capabilities in responding to evolving threats is also essential.
4. Cybersecurity Transformation
Organisations must embark on a cybersecurity transformation journey to adapt to the evolving threat landscape. According to A. T. Kearney (2020), this transformation is essential to address emerging cyber threats effectively2 Key strategies include roadmap creation by developing a customised transformation plan aligned with organisational goals and risk tolerance. Regularly simulating cyber breaches to refine incident response processes and improve resilience is vital. Empowering employees as the first line of defence by providing them with training, resources, and support to recognize and respond to cyber threats effectively is imperative.
This is where SNG Grant Thornton Cybersecurity comes in.
Why Integrate Cyber Reviews?
Integrating Cyber Reviews into your external audit process offers several key advantages:
- Holistic Risk Assessment: By combining financial and cyber risk assessments, you gain a comprehensive understanding of your organisation's overall risk profile. This enables you to make informed decisions regarding resource allocation and prioritize risk mitigation strategies effectively.
- Enhanced Audit Scope: Cyber Reviews broaden the scope of your external audit, providing valuable insights into the effectiveness of your cybersecurity controls and compliance with relevant data privacy regulations. This strengthens the overall credibility and reliability of your audit report.
- Improved Stakeholder Confidence: Demonstrating a proactive approach to cybersecurity through integrated reviews fosters trust and confidence with stakeholders, including investors, customers, and regulatory bodies.
- Proactive Threat Detection and Mitigation: Cyber Reviews can uncover previously unidentified vulnerabilities, empowering you to address them proactively before they can be exploited by malicious actors. This minimizes the risk of cyberattacks and safeguards your valuable data and systems.
SNG Grant Thornton Cybersecurity's Approach:
We offer a tailored approach to integrating Cyber Reviews into your external audit process, ensuring seamless collaboration with your existing audit team. Our experienced professionals work closely with your team to understand your specific needs and requirements, and then develop a customised review scope that complements your overall audit objectives.
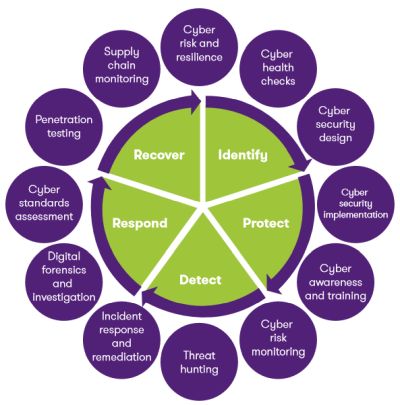
Identify: Identify cyber security risks and vulnerabilities
We help organisations understand their current exposure to cybersecurity risk and support them develop an effective security capability. Our services include cybersecurity risk and threat assessments; cyber health checks; security policy development; security process or technical assessments; and third-party and supply chain cybersecurity assurance.
Protect: Protect critical infrastructure assets
We develop and implement the technical framework and broader processes required to protect your organisation. Our services include security architecture; security technology implementations; security process design and implementation; identity and access management; privacy and data protection; GDPR and POPI advisory; data classification; enterprise application integrity; security awareness training; cyber security audits; security hardening; cloud security; vulnerability assessments; and penetration testing.
Detect: Detect the occurrence of a cyber event
We help organisations develop and implement the appropriate activities to detect the occurrence of a cyber security event. Our services include Security log review and monitoring (SOC, SIEM), Threat Hunting and Cyber Risk Monitoring.
Respond: Respond to a detected event
We work with organisations to support and monitor their cybersecurity operations and help them respond rapidly and forensically in the event of a security or data breach. Our services include digital forensics and investigations, incident response and monitoring. Our services include digital forensics and investigations, incident response and monitoring.
Recover: Recover from a cyber event
We help organisations develop and implement the appropriate activities, prioritised through the organisation's risk management process, to restore the capabilities or critical infrastructure services that were impaired through a cyber security event. Our services include advisory and assurance on business continuity management, disaster recovery and cyber insurance.
Unlocking Value: The Role of Cyber Reviews in Enhancing Audit Assurance
Cyber Reviews play a crucial role in enhancing the value and assurance provided by your external audit. They offer several key benefits:
- Increased Audit Efficiency: By integrating Cyber Reviews, your audit team can leverage our expertise and insights, potentially reducing the time and resources required for comprehensive risk assessment. This allows them to focus on core audit procedures and deliver your audit report more efficiently.
- Deeper Insights, Informed Decisions: Cyber Reviews provide valuable in-depth insights into your organisation's cybersecurity posture, enabling your audit team to make informed decisions regarding risk assessment, control testing procedures, and reporting.
- Strengthened Audit Opinion: The inclusion of Cyber Reviews in your external audit process can strengthen your audit opinion by demonstrating a more comprehensive and risk-based approach to risk assessment and control evaluation. This can enhance the credibility and reliability of your audit report in the eyes of stakeholders.
Investing in Cyber Reviews is not just an expense, but a strategic investment that enhances the value and assurance provided by your external audit, fostering greater stakeholder confidence and strengthening your overall cybersecurity posture.
Enhancing Cybersecurity Compliance with Our Services
Navigating the intricate world of cybersecurity can be challenging, especially when it comes to meeting the requirements of audit assurance. Let us explore how our tailored Cyber Reviews can empower your organisation to not only meet these requirements but also enhance your overall cybersecurity posture:
Risk Assessment Services
Our risk assessment services are designed to identify and evaluate the cyber risks your organisation faces. This is a crucial step in understanding your organisation's threat landscape and vulnerabilities. By conducting comprehensive Cyber Reviews, we provide insights into potential risks and vulnerabilities, assisting auditors in assessing the effectiveness of your cybersecurity controls. This proactive approach to risk management can enhance audit assurance by demonstrating that your organisation is actively managing cyber risks.
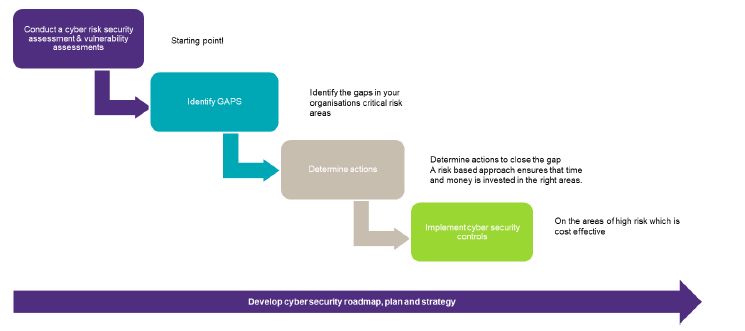
Building Cyber Resilience
We work to enhance your organisation's cyber resilience, which is its ability to prevent, withstand, and recover from cybersecurity incidents. This is not only vital for maintaining business continuity but also a key factor that auditors consider in evaluating your cybersecurity posture. Through Cyber Reviews focused on incident response preparedness and resilience testing, we help strengthen your organisation's ability to respond effectively to cyber incidents. This proactive approach can provide auditors with assurance that your organisation is resilient against potential cyber threats.
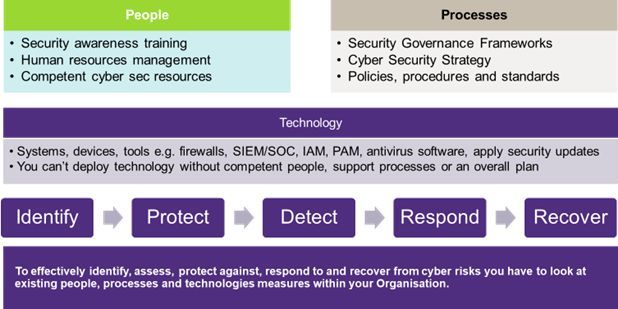
Cyber Maturity Development
We assist in developing your organisation's cyber maturity, which is its ability to manage security risks over time. A high level of cyber maturity indicates that your organisation has robust security controls and processes in place and is prepared for potential incidents. Through Cyber Reviews aimed at evaluating the effectiveness of your cybersecurity programme and maturity level, we help identify areas for improvement and guide your organisation towards greater cyber maturity. This can provide auditors with confidence in your organisation's ability to manage cybersecurity risks effectively, enhancing audit assurance and ensuring compliance with regulatory requirements.
Counting the Costs: Evaluating the Financial Implications of Cyber Reviews
The cost of your SNG Grant Thornton Cybersecurity Review will be tailored to your specific needs and the scope of the chosen review. We understand that every organisation has unique requirements, and we are committed to providing transparent pricing structures.
Factors Affecting Cost
1. Scope of the Review
The scope of the Cyber Review is a fundamental determinant of its cost. Our team collaborates closely with clients to understand their unique requirements, objectives, and risk profiles. Whether the review entails a comprehensive assessment of all cybersecurity aspects or focuses on specific areas such as vulnerability testing, compliance auditing, or incident response readiness, the breadth and depth of analysis required will influence the overall cost.
2. Type of Review
We offer a range of Cyber Review services tailored to meet diverse organisational needs, including general cybersecurity assessments, Vulnerability Assessment and Penetration Testing (VAPT), compliance audits, and incident response preparedness assessments. The complexity and sophistication of each review type, along with the specific methodologies and tools employed, contribute to variations in cost.
3. Depth of Analysis
The depth of analysis conducted during the Cyber Review directly impacts its cost. Our experienced professionals employ rigorous methodologies and advanced tools to conduct thorough examinations of clients' systems, processes, and controls. The level of detail and granularity required for the analysis, as well as the complexity of the organisation's IT infrastructure, influence the resources and time invested in the review, thereby affecting its cost.
4. Size and Complexity of the Organisation
The size and complexity of the client organisation plays a crucial role in determining the cost of the Cyber Review. Larger organisations with extensive networks, multiple locations, and diverse systems may require more extensive reviews, involving additional resources and time commitments. Similarly, organisations operating in highly regulated industries or facing unique cybersecurity challenges may incur higher costs due to the specialized expertise and tailored solutions needed to address their specific requirements.
5. Frequency of Reviews
The frequency at which clients conduct Cyber Reviews can impact the overall cost. Regularly scheduled reviews, whether conducted annually, biannually, or quarterly, may result in more predictable costs, and allow for better planning and budgeting. Conversely, ad-hoc or one-time reviews may entail additional setup and preparation costs, potentially leading to higher overall expenses.
6. Customisation and Tailoring
We understand that each client has distinct cybersecurity needs and priorities. As such, we offer customised solutions tailored to address specific concerns and objectives. The extent of customisation required, including the development of tailored review scopes, methodologies, and deliverables, may influence the overall cost of the Cyber Review. However, we believe that customisation is essential to ensure that our clients receive targeted and actionable insights that effectively mitigate their cybersecurity risks.
7. Reporting and Deliverables
The complexity and comprehensiveness of the final report and deliverables provided as part of the Cyber Review can impact its cost. We strive to deliver detailed and insightful reports that not only highlight findings and vulnerabilities but also provide practical recommendations and mitigation strategies. The level of detail, depth of analysis, and customization of reporting formats are all factors that may influence the overall cost of the review.
Conclusion: Fortifying Cybersecurity Resilience Through Strategic Partnerships
In an era defined by rapid technological advancements and escalating cyber threats, ensuring robust cybersecurity measures has become paramount. By delineating key cybersecurity challenges in 2024 and offering comprehensive strategies to address them, this paper underscores the critical role of Cyber Reviews in enhancing audit assurance. Through tailored Cyber Reviews, organisations can gain a holistic understanding of their cybersecurity posture, prioritise risk mitigation, and foster resilience.
Central to these efforts is collaboration with SNG Grant Thornton Cybersecurity, offering tailored solutions to fortify cybersecurity defences. By integrating Cyber Reviews into audit processes, organisations can navigate the complex cybersecurity landscape with confidence.
In conclusion, proactive cybersecurity measures, collaboration, and strategic partnerships are essential for fortifying defences and ensuring business continuity in the digital age. Embracing these recommendations is imperative for sustained success and resilience against evolving cyber threats.
Sources
"(ISC)² Cybersecurity Workforce Study, 2021," (ISC)², November 2021.
"Cybersecurity Talent Crunch to Create 3.5 Million Unfilled Jobs Globally by 2021," Cybersecurity Ventures, October 2018.
B. Biggio et al., "Adversarial Pattern Recognition: A Review," Pattern Recognition, Volume 88, February 2019, Pages 11-30.
"Cybersecurity Almanac 2021: 5-Year Outlook & Cybercrime Costs & Predictions," Cybersecurity Ventures.
A. T. Kearney, "Cybersecurity Transformation: The Time is Now," AT Kearney, May 2020.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.
[View Source]

