Quantum Key Distribution
Quantum key distribution (QKD) is a form of quantum cryptography that relies not on the ability of an attacker to compute hard mathematical problems, but instead the impossibility of an attacker violating the laws of physics.
QKD may be used to complement the one-time pad technique, in a similar manner to RSA as we discussed in our previous article, wherein QKD is used to secretly and securely transfer the same shared key between Alice and Bob, such that the shared key can be used to encrypt and decrypt further messages sent between them.
BB84 Protocol
The first QKD protocol developed was published in 1984 by Charles Bennett and Gilles Brassard1.
How does it work?
BB84 makes use of two principles of quantum mechanics:
- The Heisenberg Uncertainty Principle
The Heisenberg Uncertainty Principle states that, in a quantum system, only one property of a pair of conjugate properties can be known with certainty. For BB84, the polarization of photons on different bases are the relevant conjugate properties.
- The No Cloning Theorem
The No Cloning Theorem states that it is impossible to create identical copies of an unknown quantum state. The No Cloning Theorem is a direct result of Heisenberg's Uncertainty Principle, as without the No Cloning Theorem it would be feasible to create copies of a quantum state. Consequently, one property could be measured with certainty on one copy and then its conjugate property could be measured with certainty on another copy. Hence, both conjugate properties would be known with certainty, violating Heisenberg's Uncertainty Principle.
Photon Polarization
BB84 makes use of the properties of photons (particles of light). One property of a photon is its polarization. A photon may be linearly polarized in a particular basis, wherein a given basis allows the photon to be polarized in one of two possible orthogonal orientations. Hence, the polarization orientation in a particular basis allows photons to be distinguished from each other.
In the following example, and for the discussion below regarding the phases of the BB84 protocol, the bases that are used to polarize the photons are the rectilinear basis and the diagonal basis.
In the rectilinear basis, the two orthogonal orientations are aligned along horizontal and vertical axes respectively (at orientations of 0 degrees and 90 degrees to the horizontal). In the diagonal basis, the two orthogonal orientations are aligned at 45 degrees to horizontal and vertical axes respectively (at orientations of 45 degrees and 135 degrees to the horizontal).
A stream of photons which are initially unpolarized may be polarized using a polarizer. A polarizer comprises a filter that allows photons with a polarization that is aligned with the filter to pass through the filter, whilst photons with a polarization that is orthogonal (perpendicular) to the direction of the filter will be blocked (the photons may be reflected). A pair of sunglasses comprises a polarizing filter, which blocks the reflected polarized light that is polarized in a direction that is orthogonal to the polarizing filter included in the sunglasses.
An unpolarized photon that passes through a polarizer will be polarized in the same direction as the direction of the filter. For example, when unpolarized light passes through a polarizer that comprises a filter aligned in the vertical direction (90 degrees in the rectilinear basis), the photons that emerge from the polarizer will also be polarized in the vertical direction.
Three situations may occur when these vertically polarized photons encounter another polarizer:
- Polarizer is aligned: if the photons encounter a polarizer also aligned in the vertical direction, then the light will pass through.
- Polarizer is orthogonal: if the polarizer is aligned in the horizontal direction, orthogonal to the photon polarization, then the photons will be blocked.
- Polarizer is directed 45 degrees to the photon polarization: if the polarizer is neither aligned nor orthogonal to the vertical direction, but is instead at 45 degrees to the vertical direction (i.e., the filter is parallel to one of the directions in the diagonal basis) then there is a 50% chance that the photons are blocked and a 50% chance that the photons pass through. If the latter case occurs, and the photons pass through the polarizer, after the photons emerge from the polarizer the polarization of the photons will have changed to align with the direction of the filter. Hence, the photons that do pass through this polarizer will now no longer be vertically polarized, and instead will be polarized at 45 degrees to the vertical.
Hence, polarized light that encounters a polarizer may either pass through unchanged (aligned filter), be blocked (orthogonal or 45 degrees filter) or may pass through with its polarization changed to align with the polarizer (45 degrees filter).
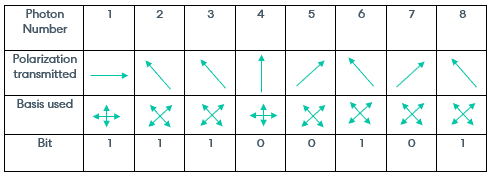
The BB84 protocol uses the polarizations of photons to create bits that may be transmitted between Alice and Bob via the photons. A bit is binary, and hence can only be represented as a 0 or 1. Similarly, the polarization of a photon in a given basis is binary. In the rectilinear basis, the polarization can be represented as 0 degrees or 90 degrees, and the polarization of a photon in the diagonal basis can be represented as 45 degrees or 135 degrees.
Therefore, a binary 0 may be represented as a photon with a polarization of 90 degrees in the rectilinear basis or 45 degrees in the diagonal basis.
A binary 1 may be represented as a photon with a polarization of 0 degrees in the rectilinear basis or 135 in the diagonal basis.
Hence, a bit can be represented by polarizing the photon in either one of the two bases.
The Process
Phase 1: Transmittal of Bits
The BB84 protocol begins by Alice transmitting to Bob a string of bits over their shared channel. The string of bits will comprise a random arrangement of 0s and 1s. The random string of bits will then be encoded onto the polarizations of a number of photons, wherein each bit will be encoded onto the polarization of one photon.
Alice can polarize a photon using a polarizer, wherein, for each photon, Alice will randomly choose either the rectilinear or diagonal basis to encode the bit onto the photon's polarization. For example, if Alice wishes to encode a 0 bit, then she will randomly choose either a polarization of 90 degrees in the rectilinear basis or 45 degrees in the diagonal basis. The table below gives an example of the bits and corresponding polarization states and basis Alice may have used.
Alice's message:
Bob will then receive the photons transmitted by Alice. To infer the bit, Bob will measure the polarization with either the rectilinear or diagonal basis (the choice of basis is up to Bob).
For each measurement Bob makes, one of two situations will occur:
- Bob coincidentally chooses the same basis as Alice. Hence, Bob measures the same polarization.
Result: Bob correctly infers the bit that Alice sent.
- Bob accidentally chooses a different Hence, the original polarization will randomly change into one of the two polarizations belonging to the basis that Bob measured the photon with.
Result: Bob has a 50/50 chance of correctly inferring the bit Alice intended to send.
Phase 2: Comparing the Basis Measurements
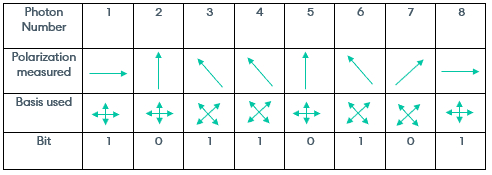
At the end of Phase 1, Bob has a list of measurements of polarization that he made and a corresponding list of the basis he used to make each measurement. The table below gives an example of the results Bob may have recorded.
Bob's Results:
Then, Bob will communicate to Alice what basis he used to measure each photon. Hence, in the table above, Bob will only report back the middle row to Alice. As Bob is not transmitting any information to Alice regarding the actual bits themselves, only what basis he used in each measurement, Bob can communicate this information to Alice over an insecure channel, as a potential eavesdropper will not be gaining any sensitive information from this message.
Alice will then notify Bob if he chose the correct basis for each photon. If Bob chose the incorrect basis for a photon, then both Alice and Bob will discard the bits corresponding to those photons. Hence, in the table above, Alice and Bob would both discard the bits corresponding to photons 2, 4, 5 and 8.
Assuming that no errors occurred, at the end of phase 2, Alice and Bob should both have the same string of bits: 1 1 1 0.
Final Phase: Key Sifting
If there are no eavesdroppers, then the string of bits obtained by Alice and Bob at the end of the first two phases would be identical. To verify that this is the case, and to identify the presence of an eavesdropper, Alice and Bob will select a sufficiently large subset of the string of bits to compare. This comparison can take place over an insecure channel, and Alice and Bob must not use these bits to form the final secret key.
Two situations can occur (assuming that the channel is perfect with no errors):
- Agreement:
If the subset of bits agree then Alice and Bob can be certain that there were no eavesdroppers. Alice and Bob will then discard the subset of bits that they compared and the remainder of the string of bits that were not compared can be used as a secret key.
Hence, Alice and Bob have securely shared a secret key with each other, with no eavesdroppers having interfered, and the key can be used for the one-time pad to encrypt further messages.
- Disagreement:
If the subset of bits disagree then this is evidence of the presence of an eavesdropper in the channel (with the assumption of no errors in the channel).
To explain the presence of disagreement between the compared bits due to an eavesdropper, consider the perspective of the eavesdropper, Eve, in the channel.
During the communication of photons with specific polarizations between Alice and Bob, Eve may intercept the photons transmitted by Alice before they are received by Bob. To determine the key, Eve has to measure the photons, and then to disguise her presence, she will then send these photons that she has now measured to Bob.
This is where the two fundamental principles of physics, the Heisenberg Uncertainty Principle and the No Cloning Theorem, can disrupt Eve's nefarious strategy.
Eve is forced to send the photons she measured to Bob, rather than sending the original set of photons sent by Alice whilst keeping a duplicated set for herself, because the No Cloning Theorem forbids Eve from being able to replicate a particle of an unknown state. The state of the photons sent by Alice is unknown to Eve until she measures them.
However, just as Bob does not know what basis Alice used to encode each bit, neither does Eve. Hence, Eve will be forced to randomly guess what the correct basis is for each photon. Consequently, for each photon, Eve has a 50% chance of choosing the incorrect basis. If Eve measures on the incorrect basis, due to the Heisenberg Uncertainty Principle, the information that was encoded by Alice using the correct basis is now lost. When Eve sends these incorrectly measured photons along to Bob, his measurement will also be random and Bob will incorrectly infer the bit with a probability of 50%.
The result of this is that the chance that Bob measures a bit incorrectly on a photon that was incorrectly measured by Eve is 50%, and the chance that a photon was measured incorrectly by Eve is also 50%. Hence, if Eve is intercepting the photons, 25% of Bob's measured bits will be different from the bits Alice encoded.
If Alice and Bob compare a large number of bits, then this 25% error in Bob's measurements compared to Alice's will become apparent, and so Alice and Bob can determine the presence of Eve, and therefore realise that their communication was intercepted.
Result
Using QKD, Alice can transmit a shared secret key to Bob by sending a string of photons where the secret key bits are encoded in the polarization of the photons, whilst also being able to detect the presence of any eavesdroppers.
The Quantum Advantage
The difference between using RSA to transmit the shared key between Alice and Bob, and using QKD to do so, is that RSA relies on the difficulty of a mathematical problem (the integer factorization problem) to provide security, whereas the security of QKD depends on the fundamental laws of quantum mechanics.
Therefore, an advantage of QKD is that the ability of quantum computers to solve hard mathematical problems poses no threat to the underlying security of QKD. This is in contrast to RSA, where a quantum computer may be developed in the future that has a number of qubits large enough to crack RSA encryption.
Another advantage of QKD is that it provides the ability to detect the presence of an eavesdropper, which is not possible using RSA. This is due to QKD using Heisenberg's Uncertainty Principle and the No Cloning Theorem to guarantee that an eavesdropper cannot measure photons and transmit them to Bob without disturbing the photon's state in a detectable way and therefore revealing their presence.
However, QKD is not without its drawbacks and challenges, which we discuss in a future article.
Footnote
1 Quantum Key Distribution – QKD (wustl.edu)
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.